Single Sign-on (SSO) authentication
There are two ways to run 4gl applications with Lycia, standard (non-secure) and secure.
When running secure applications, users have to authorize in the system by entering their logins and passwords as login and password are the credentials used for logging into the domain. In many case it is inconvenient and wearisome to go through multiple authentication procedures. Moreover, sending the credentials through the Internet might be insecure because of the risk of the 3rd party interference.
To reduce the security risks and increase usability of 4gl applications, Lycia supports the Single Sign-on technology (namely, the SSO configuration based on the Kerberos protocol).
|
|
Single Sign-on is a technology allowing access control to multiple related software systems with the same pair of credentials (login and password): After logging in once, a user gains access to a connected system or systems so that there is no need to go through several authentication procedures. |
|
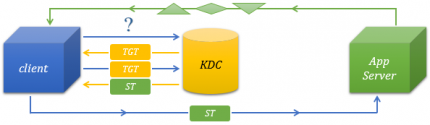
Kerberos is a standardized network authentication protocol designed to provide strong authentication for client/server applications (like web applications where the browser is the client). Kerberos protocol is based on the mechanism of the mutual authentication that allows nodes to communicate over a non-secure network after proving their identity to one another in a secure manner:
You can learn more about Kerberos here. |
With Lycia, implementation of SSO on the basis of the Kerberos protocol means that users who have logged in to the Windows domain doesn't need to re-enter their credentials to run secure 4gl applications (via the secure port).
Here is a simple diagram showing how the authentication procedure occurs with SSO in Lycia:
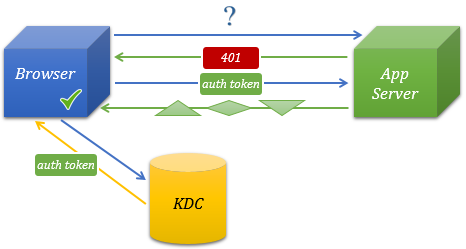
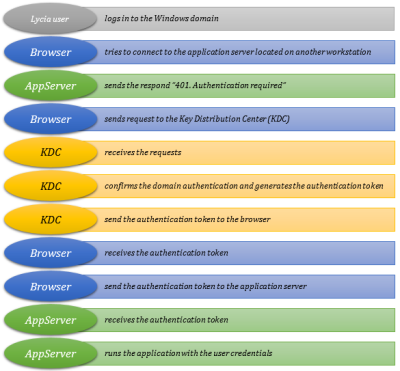
In more details, the authentication procedure follows this algorithm:
Preparing environment for SSO authentication
Before setting up the Kerberos environment, please make sure that the following requirements are fulfilled:
|
|
Client (= browser) and application server (= AppServer) are located on different computers. |
|
|
These computers belong to the same domain. |
|
|
Key Distribution Center is available within the Active Directory (= AD) server. |
|
|
SPN (= Service principal name) for the computer hosting the application server is created on the AD server. |
|
|
Browser used supports SPNEGO negotiations. |
|
|
Firewall allows exchange of the Kerberos requests between the client and the application server. |
To set up the Kerberos environment, you have to perform these sufficient steps:
|
|
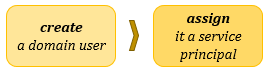
Set the necessary computer as the service principal. Service principal is principal corresponding to a network service that allows clients to verify that they are communicating with the intended service and allows services to check whether service tickets were issued by a genuine KDC. The name of the service principal has to follow this pattern: <service-name>/<hostname>@<realm> For web applications, the service principal will be: HTTP/<full qualified domain name>@DOMAIN You can refer here, here, and here to find out how service principals are set:
Here is a example of how service principals might be set: setspn -A HTTP/devel-pc3.qx.ua devel-pc3 ( |
|
|
Needs no specific configuration (full functionality is achieved with default configuration of the application server). |
|
|
Configure your browser so that it can perform the SSO authentication. The necessary details are given here for |
After these preparations, you can log in as the domain user and run Lycia applications in secure mode without entering your login and password again.
Setting up the environment for SSO authentication can be a tricky thing.
Please keep in mind these tips to make it quick and easy:
-
Be sure that your client and application server are located on different computers but in the same domain.
Otherwise, the NTML token will be sent instead of the SPNEGO one - as a result, the authentication will fail.
-
Be sure that the SPN is created on the AD server .
Otherwise, the NTML token will be sent instead of the SPNEGO one - as a result, the authentication will fail.
- Check your firewall and browser settings.
-
Be sure that the DNS name of the computer hosting the application server is the same as the one set in SPN.
Otherwise, the SPN will not be found.
- Wireshark is a useful network protocol analyzer that can come in hand if you have some issues with the Kerberos authentication and want to know whether anything went wrong.





 ,
, 
