SSH deployment
Lycia supports the SSH protocol and uses it for cross-computer and cross-system deployment.
Currently, only  →
→ and
and  →
→ SSH deployment is supported.
SSH deployment is supported.
 →
→  and
and  →
→  SSH deployment is under implementation.
SSH deployment is under implementation.
To avoid possible ambiguity between different things and notions that can be and are called server/client and SSH server/SSH client, we use these terms:
- ssh source is the computer on which the deployed application was created and built (= your development station), and
- ssh target is the computer to which you deploy your application and where you will run it.
Basic requirements
To perform SSH deployment, you must ensure that these basic requirements are fulfilled:
-
This software is installed on both ssh source and ssh target:
SSH server
Lycia – development preset for the ssh source and at least runtime-server preset for the ssh target
- Connection is set and configured between the ssh source and the ssh target.
- Both ssh source and ssh target have the same version of Lycia.
Deployment procedure
Deployment procedure is very simple and is entirely performed from LyciaStudio:
Step 0. Build the application.
After you press OK, Lycia starts deploying your application:
When SSH deployment is completed, the application and its associated files are deployed to the ssh target:
In the SSH deployment window, you specify all the necessary deployment parameters:
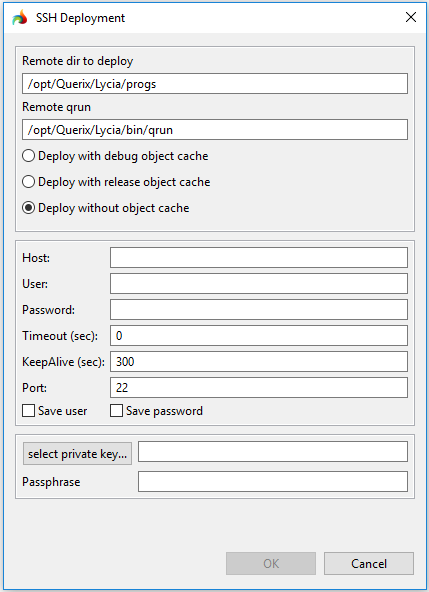
Remote dir to deploy – path to the folder where you want to deploy your application.
By default, it is

Remote qrun – path to the folder where qrun is located on the ssh target (because when we initiate the procedure of SSH deployment, we run qrun on the ssh target).
By default, it is

Deployment variants – there are three variants that differ in what type of the object_cache is built:
- SSH deployment with debug cache,
- SSH deployment with release cache, or
- SSH deployment without object_cache (by default):

Host – host name or IP address of your ssh target:

or

User and Password – username and password used to connect to the ssh target:

If necessary, you can save the username and/or password:

Port – number of the port used to connect to the ssh target (22, by default):

Private key – you can use SSH keys to connect to the ssh target instead of the user password:

SSH keys can be added by browsing or direct typing.
If the private key that you use to connect to the ssh target was created with a passphrase, you must enter this passphrase in the SSH deployment window.






